POINT SOLUTIONS
EXPLODE YOUR
CYBER RISK
by over 1,300%
POINT SOLUTIONS EXPLODE YOUR CYBER RISK
by over 1,300%

700%
Increase in internal cybersec attack surface compared to Cross Identity
Compromised cybersec systems are at least three orders of magnitude (exponentially) more dangerous than compromised SaaS tools
600%
Increase in cloud-environment & SaaS-library attack surface
1,300%
Overall increase in cyber risk
700%
Increase in internal cybersec attack surface compared to Cross Identity
Compromised cybersec systems are at least three orders of magnitude (exponentially) more dangerous than compromised SaaS tools
600%
Increase in cloud-environment & SaaS-library attack surface
1,300%
Overall increase in cyber risk

FACT CHECK
Point-solution IAM environments

- Provide ~75 % less security than Cross Identity
- Cause an additional orders of magnitude increase in environment complexity and overhead
- Require $100,000 to $1 million in ongoing System Integrator (SI) costs every year just to maintain
- Deteriorate in reliability and security with every new cybersecurity tool that you add after
FACT CHECK
Point-solution IAM environments

- Provide ~75 % less security than Cross Identity
- Cause an additional orders of magnitude increase in environment complexity and overhead
- Require $100,000 to $1 million in ongoing System Integrator (SI) costs every year just to maintain
- Deteriorate in reliability and security with every new cybersecurity tool that you add after

CYBERSEC FACTS

- Over 500 billion API attacks in 2025
- 84% of global organizations reported an API security incident in 2025
- Point IAM solutions offer no protection against non Identity-access attacks
- Actual MFA effectiveness is minimal than previously reported – mainly effective against novice attacks.
- Even intermediate-level hackers easily circumvent MFA with man-in-the-middle attacks, session hijacking, and SIM-card spoofing
- Current IAM tools remain the worst ROI investment in cybersecurity, but with the highest criticality among all cybersecurity tools
- Also because all other cybersecurity tools depend heavily on it. Identity-access is the modern language of cybersecurity that all other tools consume.
CYBERSEC FACTS

- Over 500 billion API attacks in 2025
- 84% of global organizations reported an API security incident in 2025
- Point IAM solutions offer no protection against non Identity-access attacks
- Actual MFA effectiveness is minimal than previously reported – mainly effective against novice attacks.
- Even intermediate-level hackers easily circumvent MFA with man-in-the-middle attacks, session hijacking, and SIM-card spoofing
- Current IAM tools remain the worst ROI investment in cybersecurity, but with the highest criticality among all cybersecurity tools
- Also because all other cybersecurity tools depend heavily on it. Identity-access is the modern language of cybersecurity that all other tools consume.

YOUR COMPANY’S FUTURE IS IN YOUR HANDS, AND YOUR FUTURE IN THEIRS

Sure, IT leaders so far have rarely faced scrutiny for deciding on big brand vendors.
But will that continue, when facts are revealed?
Cybersecurity must secure your environment; not provide a tool and leave you to secure it yourself.
Are CIOs really ready to take complete ownership for their IAM decision outcomes? Most say “no”. Here’s how they justify this position:
- ‘Nobody gets fired for buying IBM’
- ‘In any case, IAM is IAM, all tools are the same – it must just fit our architecture and application library’
- ‘It’s safer to go with a big name that has features we want, than to take a new product if we are not looking for those features right now’
- Huge upfront SI costs, long implementations, and continuous YoY SI maintenance costs are always expected from IAM
- ‘Cybersec vendors are the experts, not us. Failure is their fault, not ours.’
Newsflash – they are not experts, but business-motivated software vendors. They will never take even part-ownership for your security outcomes.
Additionally, 4 in 5 CIOs believe
- That IAM choice belongs to them, because they approve the procurement
But have little to no cybersecurity expertise- That is like a Chief of Justice saying ‘I know the best way to identify and capture criminals’, even though they have zero Police training.
- IAM must come from %IT budget, the same budget shared with business productivity tools
- They are saying if they live in a high-crime city, they will only invest in self-defense if their grocery budget doesn’t consume it

- Their #1 concern is that new vendors have not yet be proven business continuity, and could close-down any day
- Big brand vendors are security tool salesmen and are internally guided by business decisions. Cross Identity is a security vendor on a mission – to annihilate cybercrime. We are guided internally by security decisions.
- CIOs say it is safe to trust companies that, despite decades of market domination, have not yet produced a single cybersecurity breakthrough.
- In just 4 years, Cross Identity has delivered 5+ quantum-leap innovations, including same-genetics 7-in-1 convergence, the world’s most advanced Risk Engines, and two generations of fully Converged products.
YOUR COMPANY’S FUTURE IS IN YOUR HANDS, AND YOUR FUTURE IN THEIRS

Sure, IT leaders so far have rarely faced scrutiny for deciding on big brand vendors.
But will that continue, when facts are revealed?
Cybersecurity must secure your environment; not provide a tool and leave you to secure it yourself.
Are CIOs really ready to take complete ownership for their IAM decision outcomes? Most say “no”. Here’s how they justify this position:
- ‘Nobody gets fired for buying IBM’
- ‘In any case, IAM is IAM, all tools are the same – it must just fit our architecture and application library’
- ‘It’s safer to go with a big name that has features we want, than to take a new product if we are not looking for those features right now’
- Huge upfront SI costs, long implementations, and continuous YoY SI maintenance costs are always expected from IAM
- ‘Cybersec vendors are the experts, not us. Failure is their fault, not ours.’
Newsflash – they are not experts, but business-motivated software vendors. They will never take even part-ownership for your security outcomes.
Additionally, 4 in 5 CIOs believe
- That IAM choice belongs to them, because they approve the procurement
But have little to no cybersecurity expertise- That is like a Chief of Justice saying ‘I know the best way to identify and capture criminals’, even though they have zero Police training.
- IAM must come from %IT budget, the same budget shared with business productivity tools
- They are saying if they live in a high-crime city, they will only invest in self-defense if their grocery budget doesn’t consume it

- Their #1 concern is that new vendors have not yet be proven business continuity, and could close-down any day
- Big brand vendors are security tool salesmen and are internally guided by business decisions. Cross Identity is a security vendor on a mission – to annihilate cybercrime. We are guided internally by security decisions.
- CIOs say it is safe to trust companies that, despite decades of market domination, have not yet produced a single cybersecurity breakthrough.
- In just 4 years, Cross Identity has delivered 5+ quantum-leap innovations, including same-genetics 7-in-1 convergence, the world’s most advanced Risk Engines, and two generations of fully Converged products.

CROSS IDENTITY PRODUCTS ARE

- The right platforms to eliminate IAM shortcomings of the past
- The right platforms to quickly and reliably elevate security posture by more than ten orders of magnitude
- Right for greatly minimizing ever-bloating environment complexity and related overheads and SI costs
SO, NOW YOU HAVE NO EXCUSE
CROSS IDENTITY PRODUCTS ARE

- The right platforms to eliminate IAM shortcomings of the past
- The right platforms to quickly and reliably elevate security posture by more than ten orders of magnitude
- Right for greatly minimizing ever-bloating environment complexity and related overheads and SI costs
SO, NOW YOU HAVE NO EXCUSE

ANY IAM POINT SOLUTION, MODERN OR OUTDATED, CAUSES

- Exponential increase in complexity and repair & maintenance costs
- Frequent breakages, outages, and compromised connectors
- 15-70 new failure points as you add PAM, IGA, Access Management, CIEM, ISPM, ITDR, SOAR, SIEM, EPP, MDM, ZTNA, CSPM, DLP, and XDR to your environment
- Such failure points have been successfully breached in 84% of all global organizations in 2025
- Each additional failure point is not only in danger of a security breach, but a liable to break or malfunction – causing frequent cybersec posture downtime, organization-wide downtime, and more SI spend
- Zero new failure points when you choose Cross Identity – the only vendor who supports a 99.8% SLA
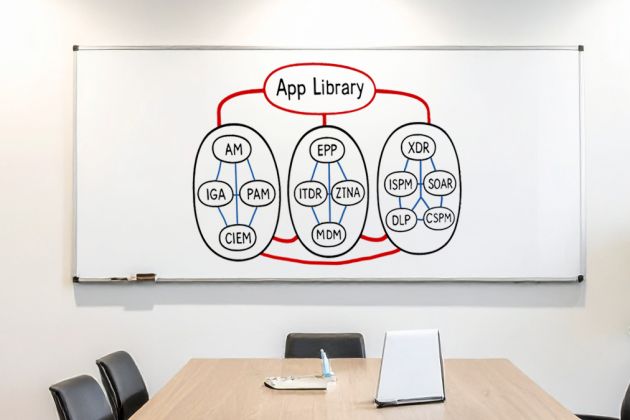
- 3-6 new API failure points with each new application onboarded
- Tens of multi-day and multi-week project timeline disruptions every year, across the entire organization
- Failed audits and compliance fines
- 1,300% increase in overall attack surface with a 700% increase in internal cybersec environment attack surface
Protect your company, and protect your career
ANY IAM POINT SOLUTION, MODERN OR OUTDATED, CAUSES

- Exponential increase in complexity and repair & maintenance costs
- Frequent breakages, outages, and compromised connectors
- 15-70 new failure points as you add PAM, IGA, Access Management, CIEM, ISPM, ITDR, SOAR, SIEM, EPP, MDM, ZTNA, CSPM, DLP, and XDR to your environment
- Such failure points have been successfully breached in 84% of all global organizations in 2025
- Each additional failure point is not only in danger of a security breach, but a liable to break or malfunction – causing frequent cybersec posture downtime, organization-wide downtime, and more SI spend
- Zero new failure points when you choose Cross Identity – the only vendor who supports a 99.8% SLA
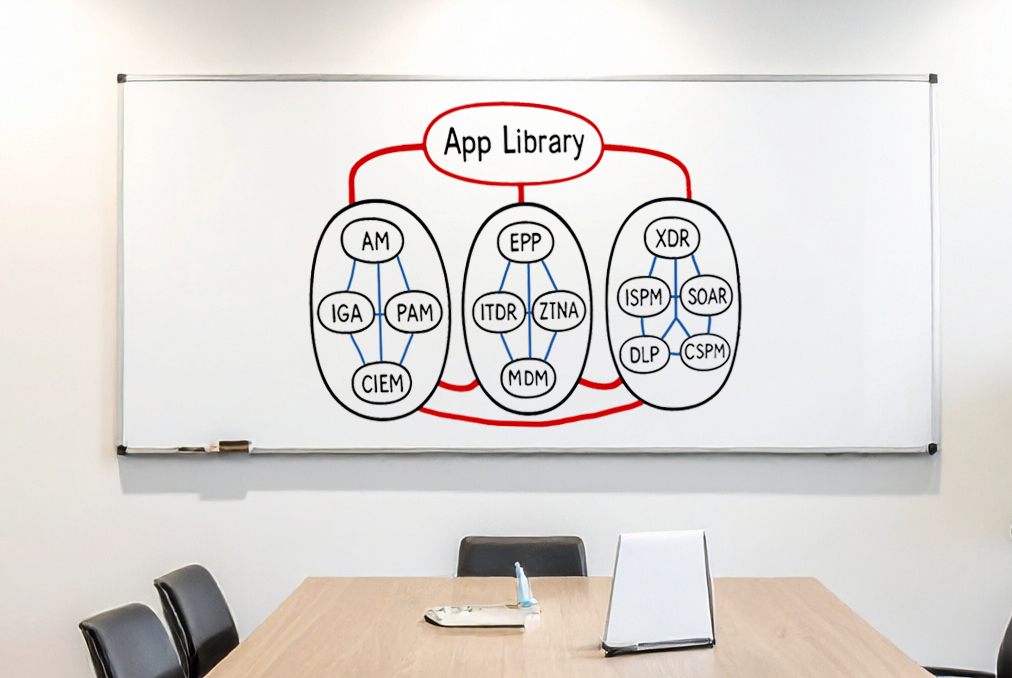
- 3-6 new API failure points with each new application onboarded
- Tens of multi-day and multi-week project timeline disruptions every year, across the entire organization
- Failed audits and compliance fines
- 1,300% increase in overall attack surface with a 700% increase in internal cybersec environment attack surface

Protect your company, and protect your career

FASTER, STRONGER, BETTER – THE COMPLETE FIGHTER

- Point solutions reduce breach risk by around 70% – but only for the Identity-access vector, and mostly for novice-level attacks
- Cross Identity reduces breach risk by 99% from day one
- Stitched environments with three or more point IAM solutions reduce breach risk by around 85-90%
- But they increase internal cybersec attack surface by up to 700%.
They also increase internal complexity, failure rates, and breaches by orders of magnitude and SaaS library attack surface by 600% - Cross Identity contributes 0% attack surface from cybersec systems and SaaS library.
- But they increase internal cybersec attack surface by up to 700%.
- Final security value of stitched Identity Fabric or IAM environments: more secure against yesterday’s threats, but reduce overall security by orders of magnitude against new threat vectors
FASTER, STRONGER, BETTER – THE COMPLETE FIGHTER

- Point solutions reduce breach risk by around 70% – but only for the Identity-access vector, and mostly for novice-level attacks
- Cross Identity reduces breach risk by 99% from day one
- Stitched environments with three or more point IAM solutions reduce breach risk by around 85-90%
- But they increase internal cybersec attack surface by up to 700%.
They also increase internal complexity, failure rates, and breaches by orders of magnitude and SaaS library attack surface by 600% - Cross Identity contributes 0% attack surface from cybersec systems and SaaS library.
- But they increase internal cybersec attack surface by up to 700%.
- Final security value of stitched Identity Fabric or IAM environments: more secure against yesterday’s threats, but reduce overall security by orders of magnitude against new threat vectors

FUTURE PROOFING IS NOT A BONUS, IT IS ESSENTIAL TO HIGH SECURITY POSTURE

Obsolescence might not render your ERP, CRM, or Project Management tool useless but an obsolete or ageing IAM platform is not only quickly useless, it
is extremely dangerous
and extremely expensive
WHEN YOU ARE FORCED TO REPLACE AGEING/OBSOLETE COMPETITOR PRODUCTS
- Long evaluation cycles again
- Lose locked-in pricing
- Expensive SI contracts again
- Same integration overhead and security gaps between multiple point tools
- If you acquire another point solution again, repeat the above three every few years
vs CROSS IDENTITY
- Cross Identity platforms have proven time and again to not only be future proof, but several generations ahead of emerging cybersecurity thoughts and best-practices
- We are on our 2nd generation of natively Converged IAM – others are just about completing their 1st generation products
- They have questionably chosen not to converge but stitch acquired point tools
- Demonstrating “fit the market” thinking, instead of improving customer security posture.
- Our Gen 1 platform Converged three years before the concept of Convergence even became a talking point, proving our ability to foresee cybersecurity trends and turns. Gen 2 (nimbleNOVA) is Converged at the genetics level.
FUTURE PROOFING IS NOT A BONUS, IT IS ESSENTIAL TO HIGH SECURITY POSTURE

Obsolescence might not render your ERP, CRM, or Project Management tool useless but an obsolete or ageing IAM platform is not only quickly useless, it
is extremely dangerous
and extremely expensive
WHEN YOU ARE FORCED TO REPLACE AGEING/OBSOLETE COMPETITOR PRODUCTS
- Long evaluation cycles again
- Lose locked-in pricing
- Expensive SI contracts again
- Same integration overhead and security gaps between multiple point tools
- If you acquire another point solution again, repeat the above three every few years
vs CROSS IDENTITY
- Cross Identity platforms have proven time and again to not only be future proof, but several generations ahead of emerging cybersecurity thoughts and best-practices
- We are on our 2nd generation of natively Converged IAM – others are just about completing their 1st generation products
- They have questionably chosen not to converge but stitch acquired point tools
- Demonstrating “fit the market” thinking, instead of improving customer security posture.
- Our Gen 1 platform Converged three years before the concept of Convergence even became a talking point, proving our ability to foresee cybersecurity trends and turns. Gen 2 (nimbleNOVA) is Converged at the genetics level.

ANALYST RECOGNITION

In just four short years, Cross Identity products have received
Strong leadership positions in major analyst’s IGA, IAG, and Access Management Leadership Matrix documents
.
Global #1 Position in CIEM Leadership Matrix documents this year
.
We feature as a leader in a larger number of IAM Leadership Matrixes than any other IAM vendor in the world. IGA, IAG, Access Management, and CIEM
ANALYST RECOGNITION

In just four short years, Cross Identity products have received
Strong leadership positions in major analyst’s IGA, IAG, and Access Management Leadership Matrix documents
Global #1 Position in CIEM Leadership Matrix documents this year
We feature as a leader in a larger number of IAM Leadership Matrixes than any other IAM vendor in the world. IGA, IAG, Access Management, and CIEM

AT A GLANCE

- Easier to implement
- Access Management, PAM, IGA, CIEM, ISPM and ITDR all in one same-genetics Converged Platform
- Beware of competitors who claim Convergence – ask them if their platforms are just pre-stitched or offer true purpose-designed Convergence.
- OneBrain™ and Warchief™ Converged risk engines supply the most advanced User, App, and Entitlement Risk Scores available today
TRULY ADVANCED, AND TRULY BUILT TO SOLVE REAL CYBERSECURITY PROBLEMS
AT A GLANCE

- Easier to implement
- Access Management, PAM, IGA, CIEM, ISPM and ITDR all in one same-genetics Converged Platform
- Beware of competitors who claim Convergence – ask them if their platforms are just pre-stitched or offer true purpose-designed Convergence.
- OneBrain™ and Warchief™ Converged risk engines supply the most advanced User, App, and Entitlement Risk Scores available today
TRULY ADVANCED, AND TRULY BUILT TO SOLVE REAL CYBERSECURITY PROBLEMS

WHERE WOULD YOU LIKE TO GO FROM HERE?

WHERE WOULD YOU LIKE TO GO FROM HERE?




