We don’t sell licenses.
We build ROI.
We secure your users, devices, and systems from identity-based attacks — with a single converged platform, without adding any overheads.
We don’t sell licenses.
We build ROI.
We secure your users, devices, and systems from identity-based attacks — with a single converged platform, without adding any overheads.
Leadership Across Core
Identity Domains
Analyst Recognition KuppingerCole
Leadership Across Core
Identity Domains
Analyst Recognition KuppingerCole
Cross Identity has been recognized by KuppingerCole for Overall Leadership across multiple core identity domains:
Identity Governance & Administration (IGA) – Leadership Compass
Identity Administration & Governance (IAG) – Leadership Compass
Cloud Infrastructure Entitlement Management (CIEM) – Leadership Compass
Access Management – Challenger
Identity Fabric –
Challenger
Only product to have all in one single code-base.
Identity Security Across Industries
Every sector faces distinct identity challenges. Cross Identity delivers vertical-specific solutions that address the precise security and compliance demands of your industry.
World’s First Natively Converged Identity Fabric
World’s First Natively Converged Identity Fabric
The Core Problem
Fragmented Suites = Integration Tax
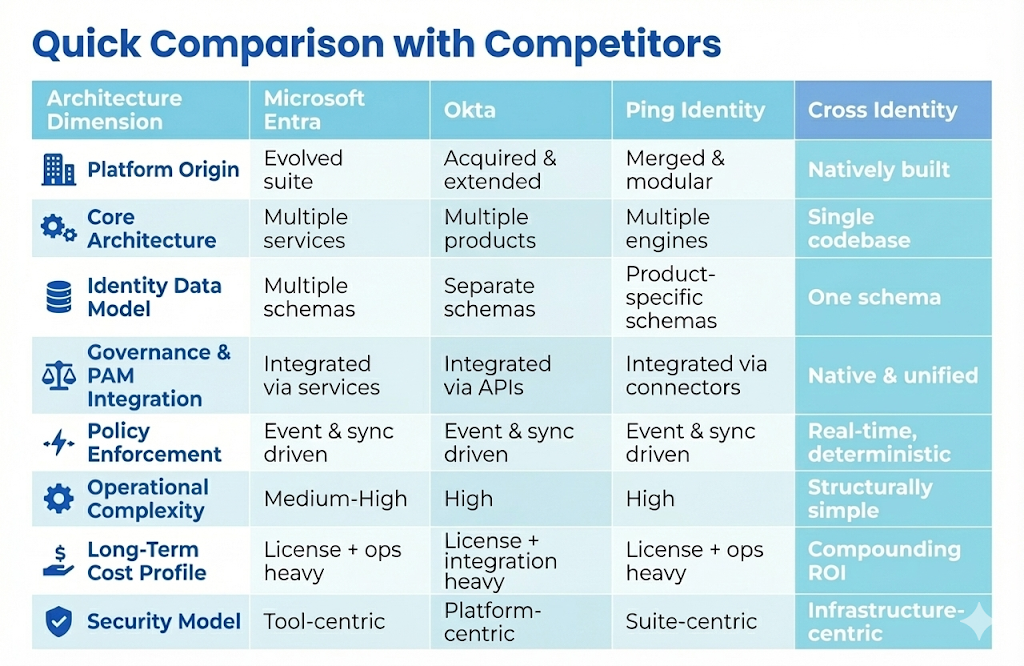
Most IAM platforms are built like Frankenstein architectures:
- Multiple acquired products
- Separate databases and schemas
- Enforcement dependent on APIs and sync jobs
This creates an integration tax, latency, operational drag, and silent security gaps.
The Architectural Shift
One DNA. One Database. One Schema.
Cross Identity is built as a single, native fabric:
- One codebase
- One identity model
- One enforcement engine
This eliminates integration overhead and enables deterministic, real-time security outcomes.
Reduce breaches | Lower IT overhead | Improve compliance visibility
Identity Risk Management (IRM)
See Risk. Stop Risk.
Attackers don’t break in-they log in. Cross Identity’s Identity Risk Management detects identity-based threats as they unfold, protecting your organization before damage occurs.
Dynamic risk detection: Identify impossible travel, new devices, suspicious IP addresses, and anomalous behavior in real time.
Context-aware scoring: Risk scoring adapts to your business reality. Configure risk levels and responses for different user populations and scenarios.
Immediate action: Block access. Require additional authentication. Suspend accounts. Notify security teams—you define the policy, we execute instantly.
Comprehensive visibility: Stop account takeover before it succeeds. Detect compromised credentials and insider threats in real time. Maintain audit trails for forensics and compliance.
The attack surface has shifted to identity itself. Cross Identity IRM delivers security that understands this reality—detecting threats across multiple dimensions and activating protection automatically.
Ready to eliminate identity blind spots? Explore how Warchief Risk Engine can transform your identity security posture.
Identity Risk Management (IRM)
See Risk. Stop Risk.
Attackers don’t break in-they log in. Cross Identity’s Identity Risk Management detects identity-based threats as they unfold, protecting your organization before damage occurs.
Dynamic risk detection: Identify impossible travel, new devices, suspicious IP addresses, and anomalous behavior in real time.
Context-aware scoring: Risk scoring adapts to your business reality. Configure risk levels and responses for different user populations and scenarios.
Immediate action: Block access. Require additional authentication. Suspend accounts. Notify security teams—you define the policy, we execute instantly.
Comprehensive visibility: Stop account takeover before it succeeds. Detect compromised credentials and insider threats in real time. Maintain audit trails for forensics and compliance.
The attack surface has shifted to identity itself. Cross Identity IRM delivers security that understands this reality—detecting threats across multiple dimensions and activating protection automatically.
Ready to eliminate identity blind spots? Explore how Warchief Risk Engine can transform your identity security posture.